As someone who has navigated the cryptocurrency world for years now, I can attest that the Lainchain scam is a stark reminder of the ever-evolving landscape of digital finance. It’s like walking through a forest filled with promising paths, only to stumble upon a wolf in sheep’s clothing – or rather, a fraudulent platform masquerading as a legitimate one.
Would you be able to identify a phishing scheme if it appeared during your upcoming gathering? Discover how Lainchain’s deception left professionals taken aback in Paris.
Table of Contents
A crypto trap in Paris
In the evening of December 3rd, a gathering for independent workers occurred at Café Oz in Paris. This event brought together professionals from diverse fields to socialize and share thoughts. One such attendee was Scott Horlacher, a skilled software engineer and designer.
The evening unfolded in an unexpected manner as two distinct characters made their entrance. One was impeccably attired, identifying himself as a lawyer managing the business aspects, while the other, a younger, rough-around-the-edges fellow, introduced himself as Leo, a developer. They both declared themselves representatives of a fresh crypto exchange platform known as Lainchain.
Horlacher’s conversation with them started off casually, as they spoke French. According to Scott, the developer referred to himself as Leo and mentioned that Lainchain was a Python Flask application. However, the responses to Scott’s technical inquiries seemed suspicious.
I asked him for details on the process of handling transactions and settling them within your exchange or platform, essentially.
The creator of Lainchain responded, “Just link your MetaMask and send it directly.” At this point, Horlacher’s doubts intensified. Upon visiting Lainchain.com, the issue became clear to him. “I moved my cursor towards the sign-up section,” he explained, “and that’s when I started to suspect, oh dear, this might be a scam.
On the registration page, there’s a built-in wallet seed generator. This suggests that the platform is handling your private keys, which poses a significant security risk at any time. It seems either incompetent or dishonest for the developers to create such a system. Given the circumstances, it appears more likely that they are operating a scam.
Following a discussion about the problem with the couple, their self-assurance started to fray. Shortly afterwards, they departed from the gathering, which left Horlacher and others to uncover the deceit, alerting others who were present as well.
In order to uncover the truth about this questionable event, crypto.news collaborated with AMLBot, a company specializing in compliance and blockchain investigations. The result was an extensive investigation which ultimately revealed Lainchain as nothing more than a skillfully planned phishing scheme.
In this piece, we delve into the conclusions drawn from the probe, explain the modus operandi of the fraud, identify key red flags to spot, and crucially, provide strategies for staying safe and avoiding such deceptive tactics in the long run.
Understanding phishing scams and their variations
Before diving deeper into Lainchain’s issue, it’s important to understand the types of phishing scams that exist and how they target victims, particularly in the financial and crypto sectors.
Phishing frauds employ deceit to persuade people into unknowingly disclosing confidential details such as passwords, recovery phrases, or digital wallet data. Instead of straight-up hacking, phishing primarily depends on manipulating human psychology, turning unsuspecting victims into accomplices in their own exploitation.
In the year 2023, it was found through Statista’s research that nearly a quarter (27.32%) of all global cyberattacks were financial phishing attacks. This is a decrease from the 36.3% reported in 2022 and a significant drop from the 41.8% recorded in 2021.
Furthermore, in the year 2023, the Federal Bureau of Investigation’s Internet Crime Complaint Center received more than 69,000 reports of financial fraud linked to cryptocurrency. The estimated total losses surpassed a staggering $5.6 billion, impacting digital assets such as Bitcoin (BTC), Ethereum (ETH), and Tether (USDT).
Phishing scams often take these forms:
- Email phishing: Generic emails impersonate trusted entities, such as exchanges, prompting users to click malicious links or share login details.
- Spear phishing: Highly targeted scams personalize messages based on specific victims, often impersonating team members or partners to establish trust.
- Clone phishing: Fake websites or apps, such as Lainchain, mimic legitimate ones, tricking users into entering their credentials or connecting wallets.
- Social media phishing: Scammers on platforms like Telegram or Twitter pose as influencers, support staff, or project representatives, enticing victims with fake giveaways or investment offers.
- Malware-based phishing: Malicious apps or links infect devices, capturing sensitive data such as seed phrases, private keys, and credentials.
Crypto phishing scams pose a significant risk due to the permanent nature of blockchain transactions – once money is sent, it’s gone forever. Being aware of these methods can help you steer clear of them.
Paying attention to potential dangers and using fundamental safety measures like two-step verification and checking the reliability of sources are essential actions for safeguarding your online possessions.
How the scam works
As a crypto investor, I initially found myself drawn to Lainchain, believing it to be a legitimate exchange. However, upon closer inspection, I uncovered some fundamental issues that revealed its questionable nature. The platform’s interface was disappointingly amateurish, with a basic design that starkly contrasted with its lofty promises. This mismatch between claims and reality left me questioning the integrity of Lainchain.
The deception started when users were asked, in what appeared to be a regular step, to link their MetaMask wallets to utilize the platform’s services. Linking wallets is often part of blockchain applications, but Lainchain misused this process. Instead of a standard authorization pop-up, they requested that users enter their seed phrases – something no legitimate platform would do, raising concerns that it might be a phishing scam.
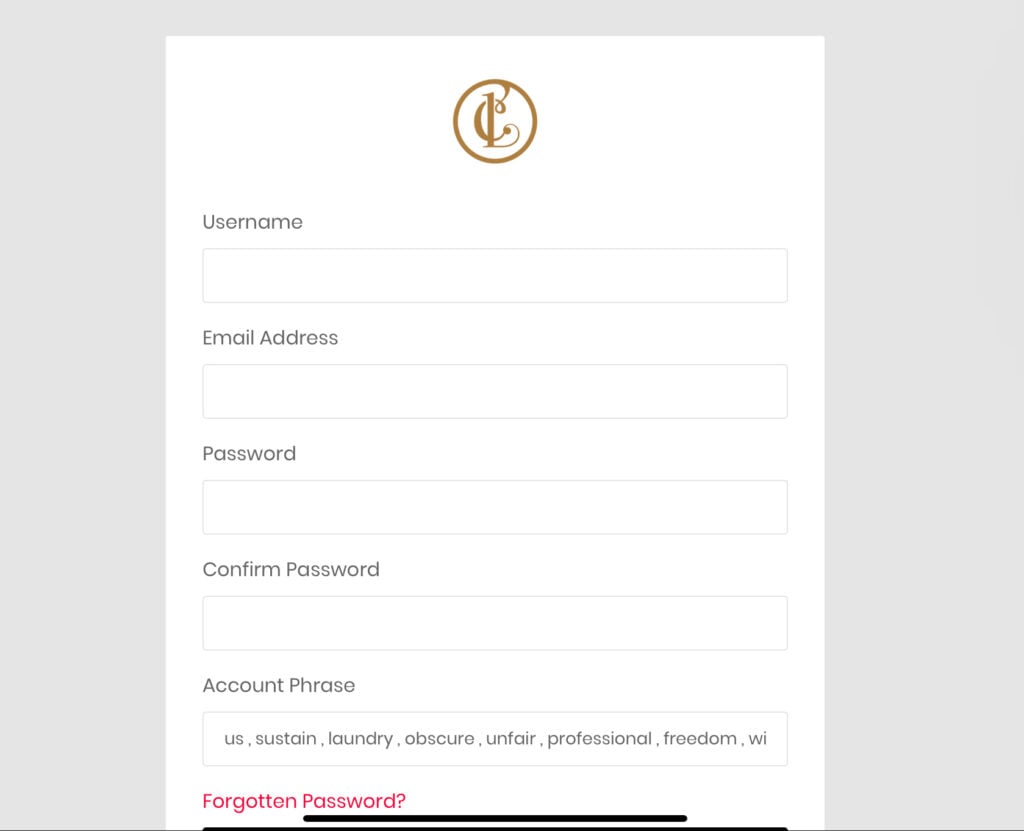
Researchers pointed out that this strategy successfully gave scammers authority over users’ digital wallets. With possession of the private keys, the wrongdoers were able to move funds at will, without being noticed or obstructed.
Instead of just outright stealing, Lainchain utilized subtle psychological tactics to expand its exploitation. Its victims were attracted by offers of exceptionally high returns and persuaded to add more funds to supposedly maximize their potential.
When people attempted to take out their funds, they ran into artificial hurdles such as requests for “processing fees” or “authentication costs,” which were merely designed to transfer additional funds from them.
The investigation also revealed that Lainchain collected personal data during registration, including email addresses and linked wallet details. This information was likely monetized further, sold on dark web marketplaces, and used for phishing campaigns or other forms of identity theft.
Technical investigation findings
Investigators using open-source intelligence methods, provided by AMLBot, successfully untangled the deceitful activities carried out by Lainchain. A significant advance was made when they scrutinized the information related to the domain registration of lainchain.com.
The domain was established using HOSTINGER, a budget registrar frequently misused by fraudsters, and privacy options were chosen to conceal the identity of the owner.
The mystery surrounding this operation’s identity is typical of cybercrime activities. Registered back on January 30, 2023, and last updated on October 30, 2024, the timeline of this domain suggests a long period during which potential victims could be targeted for fraud.
Upon closer examination, it was discovered that the site was situated on servers located in Helsinki, Finland, managed by Hetzner Online GmbH, a well-known hosting service provider known for its commitment to privacy and affordability. However, these types of services are often sought out by individuals with questionable intentions.
Additionally, the investigators discovered that Lainchain wasn’t operating in isolation, but was linked to other deceptive systems such as Rawkchain and Staxeblock. These platforms, it appears, were crafted using very similar underlying software structures.
In the HTML code of Lainchain’s website, you can find remarks that pointed directly towards Rawkchain, indicating that they were copies. This method allowed scammers to change their identity and re-launch under a new name when caught, thus tricking users further.
The examination of SSL certificates connected Lainchain to a questionable domain, finalsolutions.com.pk, implying a potential larger network for activities such as phishing or laundering illicit funds. Additionally, analysis of reverse IP lookups and DNS data exposed common servers with other suspect websites, suggesting it heavily relies on low-cost hosting and minimal maintenance.
Investigators found that Lainchain functioned as a deceptive scheme that offered great returns while minimizing costs, leveraging anonymity and technical loopholes to target users.
Fake identities and social engineering
As an analyst, one aspect that raised my concerns significantly about the Lainchain operation was their strategic deployment of pilfered identities and falsified social validation. This tactic was designed to create a sense of credibility and allure unsuspecting participants into their scam.
As reported by the investigators, Lainchain’s official site showcased pictures of individuals claimed to be team members, managers, and pioneers, all accompanied with grand job titles and detailed career histories.
It was discovered, on the other hand, that numerous images used in the scheme were actually taken from public blockchain events and personal social media accounts without permission. The con artists then deceitfully depicted these unaware people as part of the Lainchain’s executive team.
One notable instance involved the use of a familiar face belonging to a Russian politician to create a false executive identity. Additional images, originally associated with different experts in various fields, were combined with counterfeit qualifications to bolster the appearance of authenticity and credibility.
Beyond just the site, the dishonesty stretched to various platforms, such as Trustpilot. There, Lainchain presented countless positive testimonials, highlighting its intuitive design, strong safety measures, and potential for earning profits.
It turned out that a closer examination unmasked these reviews as fabricated. They appeared to come from freshly made or questionable accounts. Notably, many of these profiles showed a pattern of reviewing deceitful systems, including Rawkchain and Staxeblock in the past.
As a crypto investor, I’ve found myself unwittingly caught in a deceptive web. A clever amalgamation of misused identities, fake online personas, and glowing yet untrue endorsements created an alluring facade that lured me into trusting the platform. Unfortunately, this false sense of security left me exposed to potential financial losses and continued manipulation.
Telegram and social media analysis
The appealing privacy and user-friendly aspects of Telegram have earned it a popular spot among crypto communities, but unfortunately, it has also become a prime location for deceitful activities such as Lainchain. It was discovered that Telegram played a crucial role in the scheme, functioning as a main center to advertise the fraudulent platform and interact with victims.
In a secret online community, individuals pretending to be friendly administrators named Arin_lainchain and DanbenSpencer deceived others. They posted advertisements and steered users towards false customer service agents.
An unintentional error exposed another significant account, known as Lucifer3971, that investigators traced back to illegal activities on the black market, such as selling pilfered data. Unlike other accounts that were left unused, Lucifer3971 continued to be active, offering crucial insights.
Inside their circle, scammers craftily gave the impression of authenticity by setting up phony profiles that mimicked activity. These fictitious profiles would ask questions, post glowing testimonials, and talk about non-existent withdrawals, all aimed at making the group seem reliable. Group administrators greeted newcomers with prewritten messages and posted fabricated tales of success to entice more victims.
Instead of being limited to Telegram, the scheme expanded to other platforms like Facebook and Twitter. On Facebook, fraudsters infiltrated crypto and freelance communities with fake identities to endorse Lainchain. Meanwhile, on Twitter, they employed bots and false reviews to boost their messages, giving an impression of credibility and trustworthiness.
Data breaches and dark web activity
In a more straightforward manner, the Lainchain scam didn’t just stop at stealing money; it also targeted victims’ private information to make further profits. It was discovered that this confidential data was channelled towards massive data breaches and subsequently sold on black marketplaces hidden in the deep web.
A significant node connected within this system was the database known as naz.api, infamous for storing pilfered user information obtained through phishing scams, malicious software assaults, and web browser vulnerability exploits.
An investigation on naz.api uncovered multiple breached records connected with Lainchain, encompassing email addresses, contact numbers, passwords, and other confidential data.
The investigation also identified stealer logs connected to Lainchain. These logs, widely traded on the dark web, provided detailed snapshots of victims’ browser sessions, including saved credentials, autofill data, and screenshots of login portals.
Additionally troubling, these logs didn’t just pertain to Lainchain; they encompassed data from previous fraudulent ventures such as Rawkchain and Staxeblock. This information was accumulated in a vast network, suggesting a history of stolen data.
Protecting yourself in the crypto space
The Lainchain scam highlights the growing threat of fake platforms designed to mimic legitimate operations, targeting those unfamiliar with crypto systems. While scams like this are exposed, countless others operate undetected, stealing millions from unsuspecting users.
Staying safe starts with understanding how these scams work. Fraudsters often request seed phrases or trick users into connecting their wallets to malicious platforms. Slava Demchuk, CEO of AMLBot, explained the risks:
Linking your digital wallet to a questionable service could accidentally give risky software programs permission to take your money without you realizing it. Remember to scrutinize every transaction’s details thoroughly before confirming them. If the platform appears shady or lacks credibility, it’s often wise to avoid dealing with them.
A frequently used trick is installing fraudulent wallet apps that contain harmful software to pilfer sensitive data. Demchuk advises being vigilant when downloading apps.
Stick to trusted app providers when you’re downloading, and always review user feedback for reliability checks. Maintaining an updated antivirus program provides an additional shield against potential threats.
He also advised a skeptical approach when evaluating platforms:
Keep an eye out for warning signs such as unidentified or unconfirmed groups, absent qualifications, or discrepancies in their statements. If something seems suspicious, take a moment to investigate more thoroughly. It’s usually wise to prioritize safety over potential risks to your resources.
Reporting scams is equally important. Collaboration among users, developers, and regulators is essential to safeguarding the crypto ecosystem. Staying informed and proactive not only protects individual assets but also strengthens the broader crypto community against these threats.
Read More
- Silver Rate Forecast
- Grimguard Tactics tier list – Ranking the main classes
- USD CNY PREDICTION
- Gold Rate Forecast
- Former SNL Star Reveals Surprising Comeback After 24 Years
- 10 Most Anticipated Anime of 2025
- Black Myth: Wukong minimum & recommended system requirements for PC
- Box Office: ‘Jurassic World Rebirth’ Stomping to $127M U.S. Bow, North of $250M Million Globally
- Hero Tale best builds – One for melee, one for ranged characters
- Mech Vs Aliens codes – Currently active promos (June 2025)
2024-12-19 19:25