As a seasoned cybersecurity analyst with over a decade of experience in investigating and analyzing crypto hacks, I find ZachXBT’s thread on the WazirX hack to be both intriguing and concerning. The level of detail provided in the thread is impressive, and it seems that ZachXBT has left no stone unturned in their investigation.
As a security analyst, I’ve closely monitored the recent cyberattack on WazirX, an Indian crypto exchange, which resulted in a substantial loss of approximately $234.9 million. Noteworthy findings suggest that the Lazarus Group, a cybercrime organization with reported ties to North Korea, may be implicated in this breach.
As a crypto analyst, I recently made a discovery regarding the major security breach that occurred at WazirX. I announced my findings on X and implicated the Lazarus Group in the attack. According to my investigation, this cybercrime organization has ties to North Korean hackers.
I followed the trail of the over $230 million hack on WazirX back to its source, uncovering some intriguing insights along the way.
— ZachXBT (@zachxbt) July 18, 2024
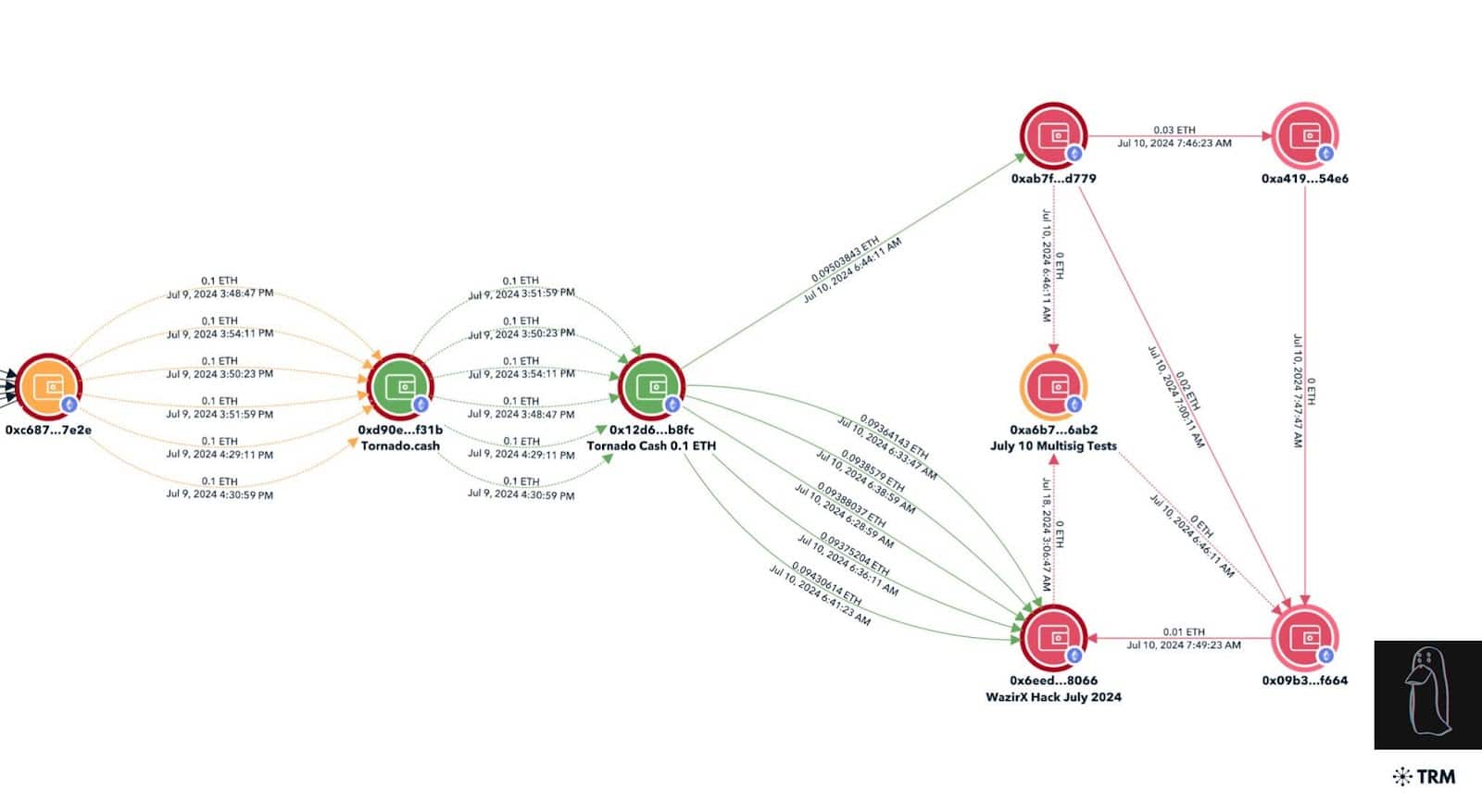
Based on the discussion in the given thread, it is indicated that the suspected hackers began their attack on July 10th. Throughout this period, they carried out trial Shiba Inu (SHIB) coin transactions between wallets ‘0x6ee’ and ‘0x09b’ using a multisig address. These experiments were financially supported by six individual transactions of 0.1 Ether each from Tornado Cash, an obfuscation service for cryptocurrencies.
ZachXBT asserted that six withdrawals of 0.1 ETH from Tornado Cash on July 10th could be linked to deposits made the day prior. This was determined by examining transactions from the address ‘0xc6873ce725229099caf5ac6078f30f48ec6c7e2e’ in detail.
On July 9th, the precision of the SHIB token tracing was validated through corroborative tests that involved a multisig wallet labeled ‘0x304’.
On July 8th, at 3:03 PM UTC, the Ethereum address ‘0xc68’ received 1 ETH from Tornado Cash. This transaction can be traced back to a deposit made nine hours prior from the address ‘0xe3b4cf64e0fc25fafb10d226984b18addc038879ed77f730abbed4737db6a5fc’.
On July 9th, the cryptocurrency addresses ‘0xc687’ and ‘0xc891’ exchanged funds with one another. This action weakens Tornado Cash’s privacy protections by establishing traceable connections between the transactions.
Looking back at the transaction record, we discover that ‘0xc891’ received 0.36 ETH and 0.66 ETH in two separate transactions on July 8th. These transactions originated from the following addresses: 0xc2fdc27f98cf02c2da2a180fa35824dc365c63795e7a7ce12ba88c1e06edd4f70xa62685d8a8b39920e957e0aaf56d527aec6d65bc9323d3d219e11f44e150e224 Therefore, these transactions funded the ‘0xc891’ address.
Analyzing the timing reveals that the transactions originated from Bitcoin addresses ‘53795dd1629026c2f92a87d5cd2447736f1afc9cae71262f3af9e62a4ac83b92’ and ‘ddfd189125ce88c622ec2453b2e9f2dbe5c5c0931f16e3389eac4976c757e5b9’. In simpler terms, these transactions came from the specified Bitcoin addresses.
The Bitcoin transactions uncover a more complex relationship between different currencies. According to ZachXBT, it appears that the Bitcoin funds originate from an undisclosed source, making it challenging to follow the trail. However, he strongly believes that the WazirX hack may be linked to the Lazarus Group based on past occurrences.
ZachXBT discovered a deposit linked to the WazirX hacker that was identified in a KYC exchange, but this finding may not significantly aid WazirX founders since such deposits can be obtained online for various exchanges. The method for investors to recover their lost funds is yet to be clarified as they continue to wait for further information from WazirX.
Read More
- USD MXN PREDICTION
- 10 Most Anticipated Anime of 2025
- Pi Network (PI) Price Prediction for 2025
- How to Watch 2025 NBA Draft Live Online Without Cable
- Silver Rate Forecast
- USD JPY PREDICTION
- USD CNY PREDICTION
- Brent Oil Forecast
- Gold Rate Forecast
- PUBG Mobile heads back to Riyadh for EWC 2025
2024-07-18 17:40