What, pray tell, is a Digital Identity? 🧐
Picture, if you will, your digital identity as that theatrical mask you parade about the internet: one part mystery, two parts drama, and entirely too revealing for comfort.
Your digital identity, dear reader, surpasses mere moniker or humble email. Nay! ’Tis the gamut—from your most extravagant social profiles, dashing crypto purse, to the dainty footprints of your daily online promenade. In this tumultuous comedy called cryptocurrency, identity theft is not just a slapstick nuisance—it’s a scene-stealer with designs on your entire fortune!
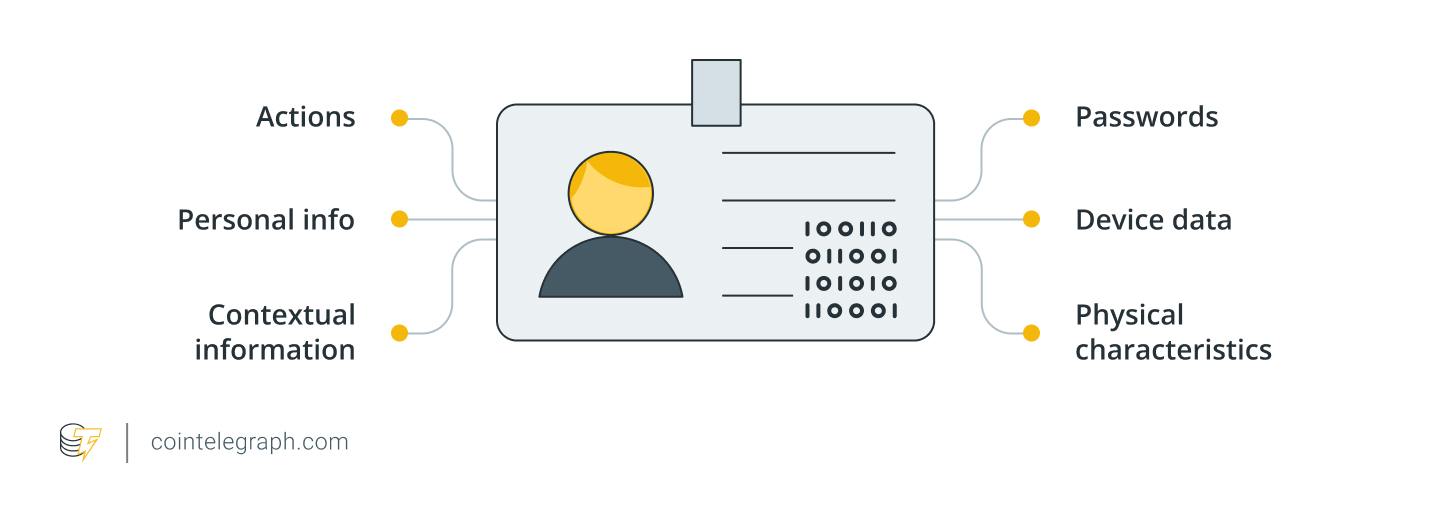
Without stout protection, the most frivolous scrap of information is but a thread—but stitch enough together and a villain will soon sport your full digital wardrobe! They’ll strut about, masquerading as you, robbing your closets, perhaps even evicting you from your own digital chateau!
Alas, many a noble soul underestimates how swift this catastrophe descends. Each fresh wallet connection, every new exchange tryst, a mere saved payment—behold, your digital silhouette swells like an actor’s ego. Information is the coin of this mad realm, and to a clever miscreant, your cyber persona glimmers like buried treasure.
Did you know? By the year 2025, pundits predict more than 50 billion digital identities will tumble into villainous hands, up 22% from last act! And who are the favorite marks? Crypto enthusiasts: those dashing, decentralized dreamers. Meanwhile, synthetic identity fraud is on the rise, striking crypto lending with the finesse of a pickpocket in a bustling Parisian crowd.
How Do These Cyber Scoundrels Pilfer Your Virtual Mask? 🤡
The rogues of cyberspace, with cunning and deceit, treat every user as a marionette, pulling strings until your secrets come tumbling down!
Phishing: A classic! A dastardly site or a too-friendly email entices you to reveal the keys to your kingdom—passwords, seed phrases, perhaps even your love for cats.
Massive data breaches spill vast ledgers of usernames, emails, and secret codes—enough material for a dozen farces!
The plot thickens with:
- Synthetic identity fraud: The chef-d’œuvre of villainy—mix a dash of truth with a smidgen of fiction, and voilà, a brand-new identity is born.
- Social engineering attacks: They woo, cajole, and flatter, until you divulge your secrets for the price of a compliment.
- Credential stuffing: They try your leaked passwords on every door, hoping you’re the sort who uses “password123” for all occasions.
Once you know the script, you’re less likely to be the comic relief to a criminal’s leading role.
Stolen Identity: Now a Star on the Dark Web Circuit 🎭
Once those knaves acquire your data, they hawk it on shadowy stages—the dark web abounds, and your tragedy is their encore!
The underworld teems with buyers for complete masquerade kits—names, emails, even your fabled crypto keys. Some villains leap into action, while others pass your identity ’round like a prop at the afterparty, staging encore performances for years hence.
Even as you slam every door shut, be assured—your stolen details are still kicking up their heels in back alleys of the web. That’s why tools such as dark web monitoring and breach alerts are your ever-vigilant doormen, never quite letting you call it a night.
Recovery is no one-act play. It’s a running gag—staying alert, checking your accounts, and waiting for the next plot twist.
Spotting the Signs: Is This Your Identity—Or Merely an Impostor? 👀
Catching the villain before the third act can save you a fortune in drama—and coin!
Has your account been locked, or worse, sent you packing? Odd transactions appear, mysterious devices crop up, and your finances prance about like they have a mind of their own.
Watch for:
- Password reset requests—ghost-written, of course.
- Frozen accounts or unexpected ejections (not the fun kind).
- New credit lines or accounts blooming like weeds in your garden.
- Cryptic withdrawals from your beloved wallets.
The sooner you spot these shenanigans, the faster you foil the plot and keep your title role!
The Comeback: What If You’re Outfoxed? Act Swiftly! 🦊
Speed, my friend! Like resolving a duel before the pistols are drawn.
If you suspect foul play, first: Secure all avenues! Change passwords everywhere, don your two-factor authentication armor, and expel all guests who’ve crashed your digital salon. Most banks and exchanges will gladly freeze your assets—treat this like a dramatic pause while you regroup.
Beyond personal heroics, alert the relevant constabulary: cybercrime units stand ready, pens poised and eager for paperwork. (Some heroes wear badges, some just hold your hand through endless hold music.)
Online help desks, too, may yet play a part! Speed and method, the pas de deux of recovery—neither is worth much alone.
Recovery Steps: Your Redemption Arc
Identity theft repair requires more than a password change. Think of it as reconstructing your reputation after a particularly scandalous farce.
After the frantic lockdown, start your vigil: comb through your bank statements, peruse crypto ledgers, and inspect your credit report—the curtain never really falls.
For an especially dramatic recovery, consider:
- Requesting fraud alerts or banishing credit agencies with a freeze.
- Hiring the digital world’s answer to a private investigator: identity recovery services.
- Insuring yourself—because who wants to foot the bill for another man’s comedy?
The road to restoration is long, sometimes filled with soliloquies. But let order and wit prevail!
Fortifying Your Virtual Boudoir: Defend Thyself, Noble User! 🛡️
Safe cyber habits are no less vital than locking your chateau at night—unless you delight in surprise company.
In this age, platforms should embrace robust, decentralized, blockchain-powered credentials. Picture it: every digital lock has its own, unforgeable key, and not even the cleverest rogue can pick it (unless they attended the right finishing school).
Unlike quaint, centralized archives (those ever-popular targets), blockchain-based identities scatter your valuables across the ether, foiling even the most determined villain. And you, wondrous user, verify yourself without baring your soul—a miracle of privacy farce!
For the careful, it’s not about ticking boxes. It’s about cultivating habits sharper than your uncle’s tongue. Try these:
- Password as cuirass: Forge unique phrases for every account; a password manager is your trusty valet.
- Double up with 2FA: If one lock is good, two are hilarious—especially to would-be thieves.
- Practice digital discretion: Every kitten post or cake-day reveal is but a clue for your adversaries.
- Pick reputable companions: Favour platforms renowned for ironclad, decentralized defense—not empty platitudes!
- Be vigilant: Set alerts, monitor with a beady eye. The earlier you spot oddities, the less you’ll have to explain at dinner parties.
- Be lavishly frugal with data: If a platform wants to know your shoe size and your mother’s nickname, show them the door.
- Eschew rookie errors: Public WiFi is the masquerade ball for hackers. Cloak yourself with a VPN, and run security checks as often as you check your hair.
Reveal less, and you’ll keep life, limb, and ledger intact!
The Encore: Update, Review, and the Farce Goes On 🔁
Maintaining your digital identity ought to be a running gag—often repeated, never stale.
Change passwords with the seasons, tinker with your security settings as if they were plot twists, and review every app, every device, every wallet connection as though they threaten to upstage you.
Add a biometric flourish—fingerprints, faces, whatever banishes the pretenders!
Those hackers, ever the enterprising troupe, lure you with fake DApps and artful phishing—resist, and steal the limelight for yourself. In this grand spectacle, vigilance is not optional. It’s survival—if not for the soul, then at least for your portfolio.
The future brims with more scenes, more masks, and endlessly inventive scripts. Fortify your digital self today, lest tomorrow’s tale be told by someone else—with your name in the credits.
Secure your internet browsing with a NordVPN subscription. [Learn more](https://pollinations.ai/redirect/432264)
Read More
- 10 Most Anticipated Anime of 2025
- Gold Rate Forecast
- Grimguard Tactics tier list – Ranking the main classes
- PUBG Mobile heads back to Riyadh for EWC 2025
- Castle Duels tier list – Best Legendary and Epic cards
- USD MXN PREDICTION
- Silver Rate Forecast
- Brent Oil Forecast
- How to Watch 2025 NBA Draft Live Online Without Cable
- USD CNY PREDICTION
2025-04-29 14:57